
Downloads:
3,640
Downloads of v 1.2.5:
1,011
Last Update:
02 Oct 2021
Package Maintainer(s):
Software Author(s):
- Oded Shimon
Tags:
network analysis tool deep processing package inspection traffic pcap password extracting map reconstruct tcp sessions hashes encrypted hashcat bruteforce- Software Specific:
- Software Site
- Software Source
- Software License
- Software Docs
- Software Issues
- Package Specific:
- Package Source
- Package outdated?
- Package broken?
- Contact Maintainers
- Contact Site Admins
- Software Vendor?
- Report Abuse
- Download
BruteShark
- 1
- 2
- 3
1.2.5 | Updated: 02 Oct 2021
- Software Specific:
- Software Site
- Software Source
- Software License
- Software Docs
- Software Issues
- Package Specific:
- Package Source
- Package outdated?
- Package broken?
- Contact Maintainers
- Contact Site Admins
- Software Vendor?
- Report Abuse
- Download
Downloads:
3,640
Downloads of v 1.2.5:
1,011
Maintainer(s):
Software Author(s):
- Oded Shimon
BruteShark 1.2.5
- 1
- 2
- 3
All Checks are Passing
3 Passing Tests
Deployment Method: Individual Install, Upgrade, & Uninstall
To install BruteShark, run the following command from the command line or from PowerShell:
To upgrade BruteShark, run the following command from the command line or from PowerShell:
To uninstall BruteShark, run the following command from the command line or from PowerShell:
Deployment Method:
This applies to both open source and commercial editions of Chocolatey.
1. Enter Your Internal Repository Url
(this should look similar to https://community.chocolatey.org/api/v2/)
2. Setup Your Environment
1. Ensure you are set for organizational deployment
Please see the organizational deployment guide
2. Get the package into your environment
Option 1: Cached Package (Unreliable, Requires Internet - Same As Community)-
Open Source or Commercial:
- Proxy Repository - Create a proxy nuget repository on Nexus, Artifactory Pro, or a proxy Chocolatey repository on ProGet. Point your upstream to https://community.chocolatey.org/api/v2/. Packages cache on first access automatically. Make sure your choco clients are using your proxy repository as a source and NOT the default community repository. See source command for more information.
- You can also just download the package and push it to a repository Download
-
Open Source
-
Download the package:
Download - Follow manual internalization instructions
-
-
Package Internalizer (C4B)
-
Run: (additional options)
choco download bruteshark --internalize --source=https://community.chocolatey.org/api/v2/ -
For package and dependencies run:
choco push --source="'INTERNAL REPO URL'" - Automate package internalization
-
Run: (additional options)
3. Copy Your Script
choco upgrade bruteshark -y --source="'INTERNAL REPO URL'" [other options]See options you can pass to upgrade.
See best practices for scripting.
Add this to a PowerShell script or use a Batch script with tools and in places where you are calling directly to Chocolatey. If you are integrating, keep in mind enhanced exit codes.
If you do use a PowerShell script, use the following to ensure bad exit codes are shown as failures:
choco upgrade bruteshark -y --source="'INTERNAL REPO URL'"
$exitCode = $LASTEXITCODE
Write-Verbose "Exit code was $exitCode"
$validExitCodes = @(0, 1605, 1614, 1641, 3010)
if ($validExitCodes -contains $exitCode) {
Exit 0
}
Exit $exitCode
- name: Install bruteshark
win_chocolatey:
name: bruteshark
version: '1.2.5'
source: INTERNAL REPO URL
state: present
See docs at https://docs.ansible.com/ansible/latest/modules/win_chocolatey_module.html.
chocolatey_package 'bruteshark' do
action :install
source 'INTERNAL REPO URL'
version '1.2.5'
end
See docs at https://docs.chef.io/resource_chocolatey_package.html.
cChocoPackageInstaller bruteshark
{
Name = "bruteshark"
Version = "1.2.5"
Source = "INTERNAL REPO URL"
}
Requires cChoco DSC Resource. See docs at https://github.com/chocolatey/cChoco.
package { 'bruteshark':
ensure => '1.2.5',
provider => 'chocolatey',
source => 'INTERNAL REPO URL',
}
Requires Puppet Chocolatey Provider module. See docs at https://forge.puppet.com/puppetlabs/chocolatey.
4. If applicable - Chocolatey configuration/installation
See infrastructure management matrix for Chocolatey configuration elements and examples.
This package was approved as a trusted package on 03 Oct 2021.

BruteShark is a Network Forensic Analysis Tool (NFAT) that performs deep processing and inspection of network traffic (mainly PCAP files). It includes: password extracting, building a network map, reconstruct TCP sessions, extract hashes of encrypted passwords and even convert them to a Hashcat format in order to perform an offline Brute Force attack.
The main goal of the project is to provide solution to security researchers and network administrators with the task of network traffic analysis while they try to identify weaknesses that can be used by a potential attacker to gain access to critical points on the network.
Two BruteShark versions are available, A GUI based application (Windows) and a Command Line Interface tool (Windows and Linux).
The various projects in the solution can also be used independently as infrastructure for analyzing network traffic on Linux or Windows machines. For further details see the Architecture section.
The project was developed in my spare time to address two main passions of mine: software architecture and analyzing network data.
I love to get feedbacks from BruteShark users, your opinion is important to me!
Feel free to contact me on <[email protected]> or create new issue.
Please ⭐️this repository if this project helped you!
What it can do
- Extracting and encoding usernames and passwords (HTTP, FTP, Telnet, IMAP, SMTP...)
- Extract authentication hashes and crack them using Hashcat (Kerberos, NTLM, CRAM-MD5, HTTP-Digest...)
- Build visual network diagram (Network nodes & users)
- Reconstruct all TCP Sessions
- File Carving
Examples
Videos
How do i crack (by mistake!) Windows 10 user NTLM password
Run Brute Shark CLI on Ubuntu with Mono
Hashes Extracting
Building a Network Diagram
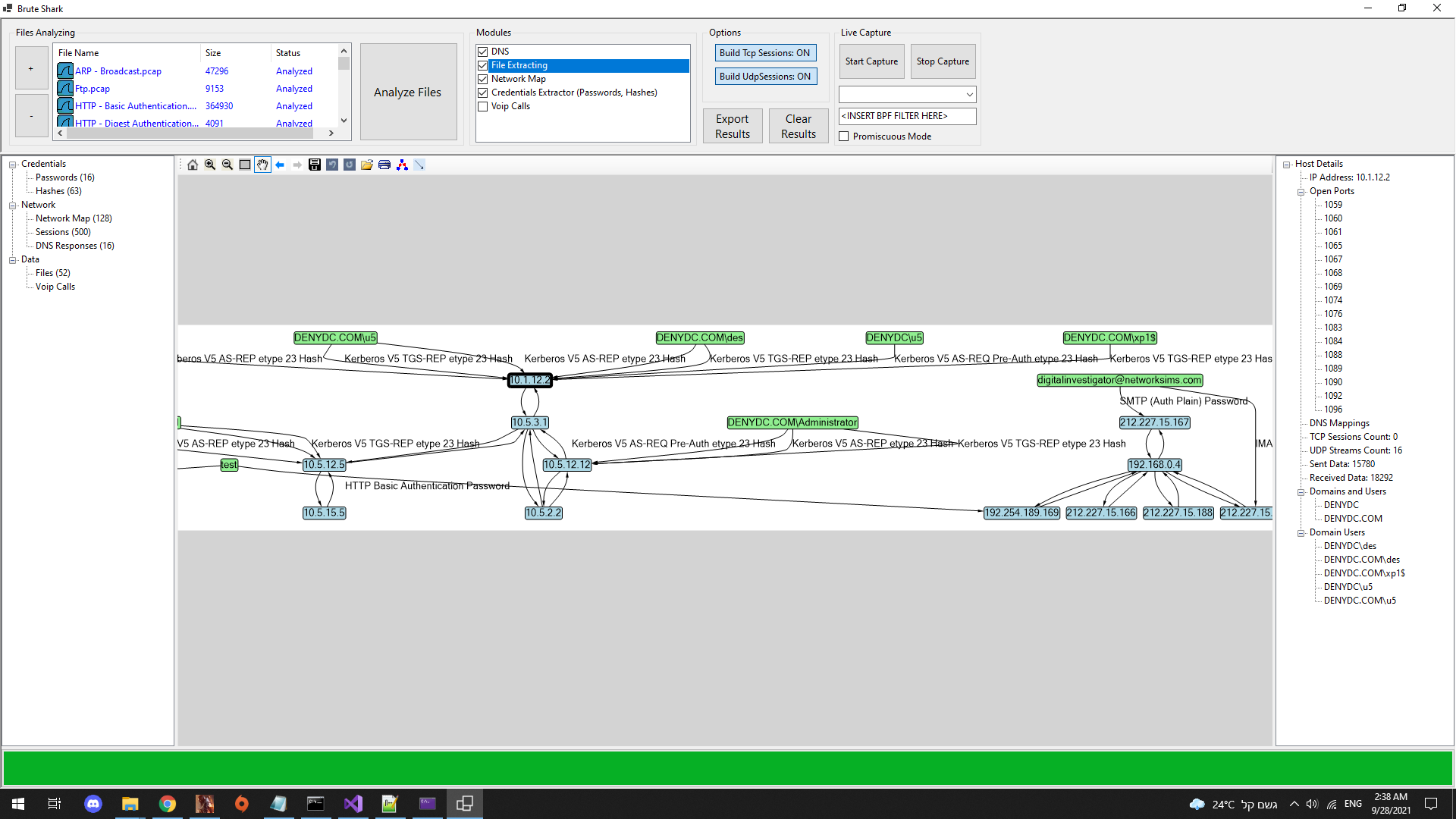
File Carving
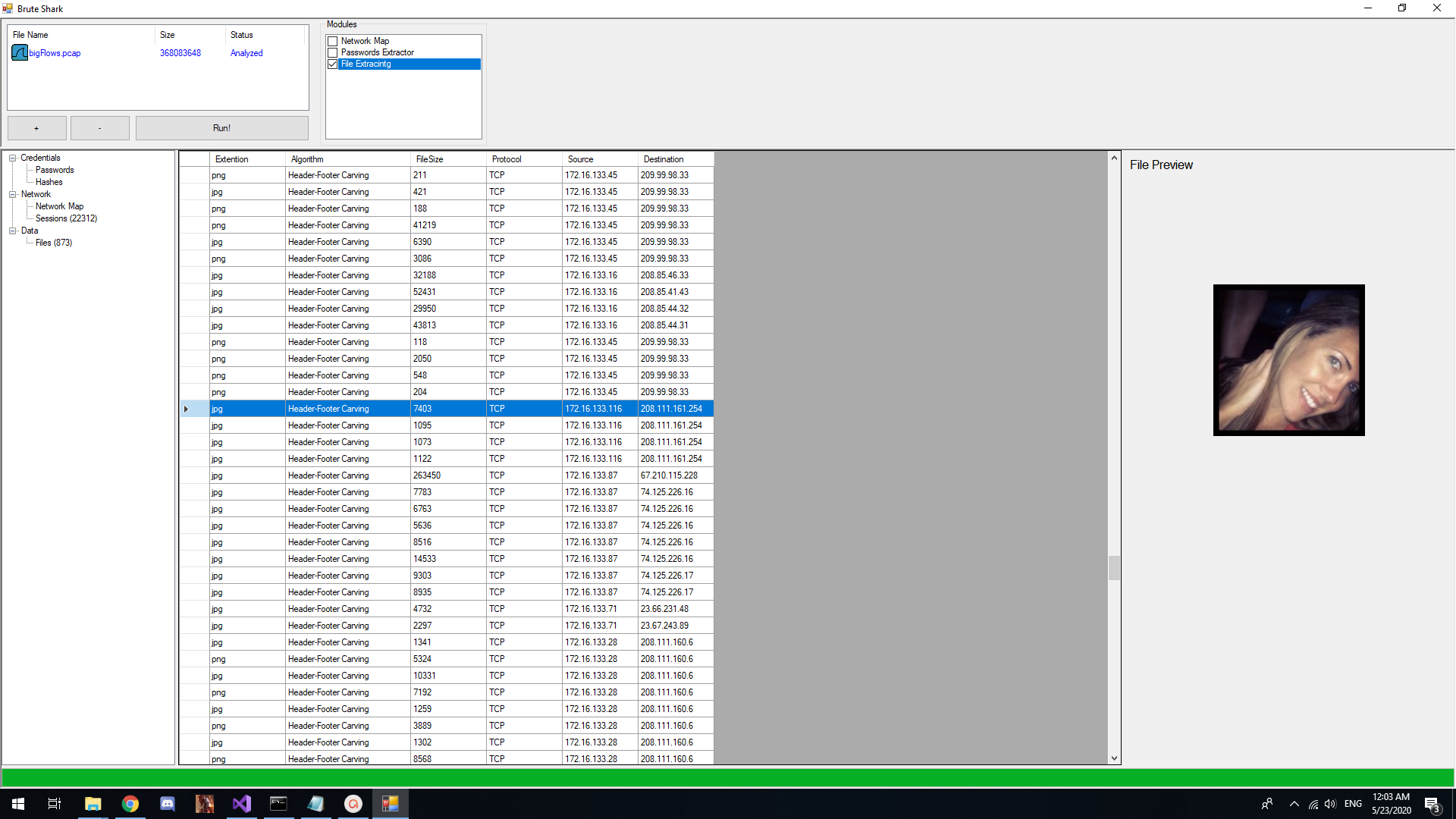
Password Extracting
Reconstruct all TCP Sessions
Brute Shark CLI
Please Note: This is an automatically updated package. If the package is outdated for more than two days, please let me know!
Log in or click on link to see number of positives.
- bruteshark.1.2.5.nupkg (101e50cd2080) - ## / 61
- BruteSharkDesktopInstaller_x64.msi (ff9a4ecce0af) - ## / 57
In cases where actual malware is found, the packages are subject to removal. Software sometimes has false positives. Moderators do not necessarily validate the safety of the underlying software, only that a package retrieves software from the official distribution point and/or validate embedded software against official distribution point (where distribution rights allow redistribution).
Chocolatey Pro provides runtime protection from possible malware.
| Add to Builder | Version | Downloads | Last Updated | Status |
|---|---|---|---|---|
| BruteShark 1.2.5 | 1011 | Saturday, October 2, 2021 | Approved | |
| BruteShark 1.2.4 | 161 | Thursday, September 16, 2021 | Approved | |
| BruteShark 1.2.3 | 133 | Thursday, September 2, 2021 | Approved | |
| BruteShark 1.2.2 | 517 | Sunday, May 2, 2021 | Approved | |
| BruteShark 1.2.1 | 250 | Monday, April 12, 2021 | Approved | |
| BruteShark 1.2.0 | 324 | Tuesday, March 9, 2021 | Approved | |
| BruteShark 1.1.6 | 237 | Tuesday, January 26, 2021 | Approved | |
| BruteShark 1.1.5 | 124 | Saturday, January 23, 2021 | Approved | |
| BruteShark 1.1.4 | 193 | Saturday, January 9, 2021 | Approved | |
| BruteShark 1.1.3 | 167 | Tuesday, December 15, 2020 | Approved | |
| BruteShark 1.1.2 | 93 | Tuesday, December 1, 2020 | Approved | |
| BruteShark 1.1.1 | 260 | Wednesday, September 2, 2020 | Approved | |
| BruteShark 1.1.0 | 127 | Tuesday, August 25, 2020 | Approved |
Oded Shimon
-
- wireshark (≥ 3.2.4)
- dotnetcore (≥ 3.1.7)
Ground Rules:
- This discussion is only about BruteShark and the BruteShark package. If you have feedback for Chocolatey, please contact the Google Group.
- This discussion will carry over multiple versions. If you have a comment about a particular version, please note that in your comments.
- The maintainers of this Chocolatey Package will be notified about new comments that are posted to this Disqus thread, however, it is NOT a guarantee that you will get a response. If you do not hear back from the maintainers after posting a message below, please follow up by using the link on the left side of this page or follow this link to contact maintainers. If you still hear nothing back, please follow the package triage process.
- Tell us what you love about the package or BruteShark, or tell us what needs improvement.
- Share your experiences with the package, or extra configuration or gotchas that you've found.
- If you use a url, the comment will be flagged for moderation until you've been whitelisted. Disqus moderated comments are approved on a weekly schedule if not sooner. It could take between 1-5 days for your comment to show up.









 Ansible
Ansible

 PS DSC
PS DSC

